This blog is for users of the Microsoft Windows Operating System, it contains tips, tricks and secrets for both beginner and expert users.
Friday, December 29, 2006
Software: Installing DirectX
To find out what version of DirectX your system is using, from the Run... command type "dxdiag" and press Enter. This will run the DirectX Diagnostic Tool, and display information about your computer's hardware and the version of the OS and software that its running.
To obtained the latest version of DirectX visit the Microsoft DirectX site.
Thursday, December 28, 2006
Internet Radio Sites
- AOL Radio (featuring XM Radio content)
- Live365.com
- Pandora.com
- Yahoo! Music
Wednesday, December 27, 2006
Internet Explorer: Automatically Clearing the Cache
There are two reasons some people don't like these file stored on their hard drive. First and foremost for privacy reasons, and second because it can consume a lot of space.
You can manually clear the cache from the Tools menu, by selecting Internet Options. Then on the General tab, pressing the Delete Files button. You can also configure IE to automatically clear the browser cache when you exit the program.
- From the Internet Options dialog, select the Advanced tab.
- In the Setting listbox, under the Security section, check 'Empty Temporary Internet Files folder when browser is closed'.
- Press the OK button.
Tuesday, December 26, 2006
Free (and low cost) Privacy Toolkit (Updated)
File/Disk Encryption
What privacy toolkit would be complete if I didn't talk about encryption. There are several tools available that allows you to encrypt your data. One of the best tools for encrypting your data is GnuPG, it uses strong encryption to protect your data. (Note: This tool is difficult to use so make sure that you download one of the the GUI interfaces for it.)
If you own Windows XP Professional, it includes a built-in file encryption function called EFS that is part of the OS. EFS will automatically encrypt and decrypt your files for you.
If file encryption is not enough, and you want to encrypt the contents of your whole hard drive use a program called TrueCrypt. TrueCrypt works by creating a virtual encrypted disk within a file and then allows you to mount it like a real hard drive.
Other privacy tools and resources:
- SDelete: Completely erases a file on the hard drive by writing data over it several times.
- DBAN: Completely erases a whole hard drive by writing data over it several times.
- CCLeaner: Windows privacy and optimization utility, read this page for a list of features.
- Firefox: Clearing The Cache: Explains how to clear the private information from the Firefox browser.
- Internet Explorer: Clearing The Cache: Explains how to clear the private information from the Internet Explorer browser.
Find Out What Web Sites Know About You
Check out the following sites if you want to see the data someone can learn about you, just by querying your IP address or your browser's information.
- GeoBytes: Once someone has your IP address, then they can use it isolate where your ISP is located. So if you live in a close proximity to your ISP then someone can roughly narrow down where you live.
- CGI Environment Variable Viewer: The information shown on this page, displays what just about any web server can learn about you based on HTTP header information your browser sends every time you visit a web site. Things to notice are the REFERRER and USER AGENT information. The referrer can display the web site you were previously at before visiting the site. The user agent shows the site the type of browser you're using.
- HTTP Header Viewer: See the HTTP headers supplied by your browser to every web site that you visit.
- BrowserSpy: This web site will show you just about everything that a web site can query about your browser.
If you would like to browse the web semi-anonymously, check out EFF's Tor tool. This tool protects your privacy by, using a technology called 'Onion-Routing' which basically means that it adds several 'layers' of extra network routing to obfuscate the origin of the traffic.
If Tor is too complicated to use a good alternative to browse anonymously is a service called Anonymizer (Note: this is a fee-based service). This service works by performing your HTTP requests for you, then sending you back the results. The only thing that the visiting web site sees is the Anonymizer servers.
If you want to test if these services are really working, go to a site called WhatsMyIPAddress.com before turning on the service. Then visit the web site again after you enable the service. Your IP address should be different, if not then the service is not working for you.
Other privacy tools and services:
- HushMail: Secure e-mail service (free/fee services).
- Hush Messenger: Secure instant messaging.
- SSLCheck: Checks the strength of the encryption supported by your browser.
- Zfone Project: Secure VoIP phone software.
- Free S/MIME Certificate: Allows you to send secure email or digitally sign your e-mail messages.
- TrackMeNot: Help protects against data profiling popular search-engines by issuing randomized queries with fake data.
- PrivacyBar: Provides a set of privacy and security tools for Firefox.
- Free eBook: Defending Yourself in the Information Age
- Internet Privacy is an Oxymoron
- Welcome to the Internet, Now Go Home
- ACLU Pizza (this video is very disturbing and funny at the same time)
Monday, December 25, 2006
Web Site: StopBadware.org
Currently there are 412+ reports of 'bad software' on the site. I hope to see more added soon, this could be a valuable resource if people contribute to it.
Below is an excerpt from the site: "StopBadware.org is a "Neighborhood Watch" campaign aimed at fighting badware. We will seek to provide reliable, objective information about downloadable applications in order to help consumers to make better choices about what they download on to their computers. We aim to become a central clearinghouse for research on badware and the bad actors who spread it, and to become a focal point for developing collaborative, community-minded approaches to stopping badware." Read more.
Thursday, December 21, 2006
Free (and low cost) Privacy Toolkit
Then there are the web sites that force you to register your personal information in order to access content on it. If you're not a regular visitor of that site, or it's a site that you don't trust then you might be leery of giving out this information to them.
What if I told you there was a way to protect your privacy, while still allowing people the ability to contact you when they want to. There are several web sites on the Internet that offer free or low-cost services that can help protect your privacy.
Disclaimer: Use the tools and services listed below at your own risk. I do not recommend or endorse any of the companies, services, or software listed below. The information on this site is provided for general reference purposes only.Creating a Public E-mail Address
The first thing that you need in your privacy toolkit is a public email address, one that you don't mind giving out to people, companies, web sites, or publishing on the Internet. This address is basically going to be your first line of contact for people whom you don't know and web sites that you don't trust.
Several companies such as Google's Gmail, Yahoo's Yahoo Mail, Microsoft's Windows Live Mail, etc. offer free email addresses with SPAM filtering, file attachment virus scanning, etc. The main issue about having this extra account is that you're going to have to check it on a regular basis in order to maintain it.
Avoiding Web Site Registration
If you hate registering at web sites that you almost know that you will never visit again or visit infrequently there are two tools that I would suggest. The first is called BugMeNot, this site has generic user names and passwords for popular web sites that you can use so you don't have to register.
The second web site I want to suggest is one called 10-Minute Mail. This site gives you a disposable e-mail address that only lives for 10 minutes. After the time expires the email address and messages are automatically deleted.
Real World Privacy
What about those times when you need to receive or make a phone call, or fax. There are a few sites that can offer you a solution.
The first site is called PrivatePhone, which offers to give you a free local phone number that people can leave you messages. The voice mails that you receive through this service will be mail to your email account.
If you need to receive faxes there is a service called jConnect, that gives you a phone number for people to send faxes to. The faxes that you receive through this service will be mail to your email account.
If you need to make calls to other people, check out Skype's SkypeOut service. If you need a public phone number to receives calls use the SkypeIn feature. Note: there is a cost associated with sending and receiving calls using this service.
Wednesday, December 20, 2006
Firefox: Critcal Patch Released Today...
This update fixes flaws with the RSS feeds, and problems JavaScript in e-mail. Also as part of the Firefox update several bugs have been fixed to improve the stability of the software.
Note: Mozilla recommends that users disable JavaScript in Thunderbird to prevent unauthorized code from affecting their systems.
Monday, December 18, 2006
Windows XP: Swap File (Virtual Memory) - Part 2
Optimizing the Swap File
The default Windows VM settings will work fine for most people. Although, there are still a few ways to optimize the swap file, but in reality they will only offer small amounts of extra performance. So for most people the time required to make these changes might not be worth the effort.
For the real system performance fanatics, I will show you some ways to make your system work more efficiently.
- Note: None of these changes should cause irreversible damage to your system, but I aways recommend that you have a good back up of your data before proceeding with system changes. Also as always proceed at your own risk.
- From the Start Menu, right-click on My Computer and select Properties
- Click the Advanced tab, and press the Settings button in the Performance section.
- Click on the Advanced tab again, then press the Change button.
Note: The general rule of thumb for setting the size of the swap file is about 1.5-2 times the size of your physical RAM.Trick 2: After turning off the automatic growth feature (in Trick 1), defragment swap file. This can be done using the Windows Defragment tool. This will make the file contiguous and prevent your computer from having to seek all over the hard drive to get the data it needs.
Trick 3: If you have multiple hard drives (and I don't mean multiple partitions on the same drive) installed on your computer. Consider moving the swap file to the non-system drive. This way the computer can access multiple drives at the same time.
Trick 4: If you have enough physical RAM installed on your computer (generally 2GB or more), you might want to consider turning off the VM feature. This will help your computer's performance because it doesn't have to manage the swap file. In the VM dialog, select the 'No paging file' radio button, and press the OK button.
Friday, December 15, 2006
Windows XP: Swap File (Virtual Memory) - Part 1
The way the VM feature works is by moving non-critical chunks of data out of the computer's RAM, and on to the hard drive thus free up memory for other things. This process known as 'swapping' or 'paging'.
The benefit of VM is that it gives you more memory to run your applications if you don't have enough physical RAM. The problem is that in order to get the extra memory, VM has to store the data from the faster RAM on to the slower local hard drive.
All hard drives are much slower then real physical RAM. So when the system requests a chunk of memory from VM, the computer has wait for data to come from the hard drive. This will make your seem much slower then it actually is.
When the VM data is written to disk, its stored in a file called C:\PAGEFILE.SYS. This file is generally x1.25 to x1.5 the size of your RAM. So if you have 1GB of RAM, the swap file will consume about 1.25 to 1.5GB of hard drive.
Over the next few days we will discuss options for managing and optimizing virtual memory.
Thursday, December 14, 2006
Article: Skype Replaces Free SkypeOut Calls With Flat Rate
Skype as has always been a pretty good deal, but it has just gotten better when I read this article. PC Magazine reports: "On Wednesday, Skype announced it will be offering U.S. and Canadian customers a new unlimited calling plan at a flat rate of $29.95 per year, or, for those who decide to subscribe before January 31, 2007, $14.95. ... The Skype Unlimited Calling plan will let users make 12 months of unlimited SkypeOut calls to any phone in Canada or the U.S. and, according to the company, is the first time that Skype is making an annual calling plan available anywhere in the world."
So, if you frequently call people within the United States or Canada (even if you live in other parts of the world), you can call any phone in that region, for an unlimited amount of time, as many times as you want for $14.95 for the first year (if you sign up before January 31, 2007). The catch is that you have use your computer to make the calls.
I expect that this could cause a price war with the other major VoIP carriers such as Vonage, AT&T, etc.
Tuesday, December 12, 2006
Security: Microsoft Patch Tuesday (December)
For the average user, if you have Automatic Updates enabled your computer will download these updates for you in the background. Then when you shutdown these patches will be applied to your system. If you leave your computer on overnight they will automatically be installed and your system rebooted if necessary.
Warning: Before you leave your computer at night make sure you save all your work or it will be lost if your system has to be rebooted.
Enabling Automatic Update
If you don't have 'Automatic Updates' turned enable I would suggest that you turn it on as soon as possible. If you don't want to enable Automatic Updates, you can always update your computer by visiting the Windows Update site and downloading and installing the patches manually.
To enable Automatic Updates:
- From the Start menu, select the Control Panel folder.
- Double-click the System applet in the control panel folder.
- Click the 'Automatic Updates' tab.
- Check the 'Automatic (recommended)' option. (optional: if you don't like this feature, you can set it to: 'download but not install the update', 'just notify you', or 'disable this feature altogether' [not recommended])
- Press the OK button when done.
Note: For the latest Microsoft Security Bulletins, check out this site.
Monday, December 11, 2006
Software: NASA World Wind (3D Interactive World Viewer)
NASA World Wind 1.4 Promo Video
This video only uses graphics from within World Wind no post processing has been done, except for joining video clips together and adding audio.
Note: NASA World Wind 1.4 is not yet available, currently 1.3.5 is available for download.
Friday, December 08, 2006
Software: FreeBASIC compiler
For more information check out the web site, or click the following link to see a list of features.
Happy programming...
Thursday, December 07, 2006
Software: AudioShell
If you want more information about audio file tags (such as: ID3), check out the following site. Below is a excerpt from the site: "Digital audio files can contain, in addition to the audio track, related text and/or graphical information. The information you're probably familiar with take the form of Song title, Artist name, Album name, Year and Genre. This is the information displayed when you playback a digital audio file on your computer or portable device."
Wednesday, December 06, 2006
Article: Hands-on with Belkin's Cable-Free USB Hub
I generally don't cover hardware in this blog, but this is one of those new technologies that I have been waiting to come out. I never thought I would like using a cordless mouse or keyboard until I started using one at work. I like not having deal with those wires.
At home I am primarily a laptop user, so if I have to hook any wires up to the computer on a regular basis its a pain. Although if I break down an get a docking station it would solve a lot of problems.
Now the point, this technologies may one day help reduce the rat nest of wires that most computers have hanging down behind them. If would be nice if everything was just wireless. Although this could create a lot of security issues that I don't even want to get into.
Tuesday, December 05, 2006
Security: NSA Windows XP Security Configuration Guides
Monday, December 04, 2006
Windows XP: Disable or Enabling Windows Shares
The problem with network share if you don't manage the security permissions on them properly, you can accidentally expose files to others you may not intended to. In this article I talk about how to disable this feature for those who don't want to use it. Or by using almost the same procedure you can enable this option if it has been disabled.
To enable or disable Windows shares:.
- From the Start menu, open the Control Panel folder.
- Open the 'Network Connections' folder.
- Right-click the active network connection (i.e.: 'Local Area Connection') and select Properties.
- To disable this feature uncheck (or to enable it check) the 'File and Printer Sharing for Microsoft Networking' checkbox.
- Press the OK button when done.
Friday, December 01, 2006
Article: Recycling E-Waste
I have been wanting to write an article about this subject for a long time but have not gotten around to it. The author of this article did a great job of emphasizing the problem.
The problem is that our society has such a deposible mentality, that we don't think about the consequences of throwning that piece of old electronics in the garbage. We need to change our views on this issue, out of site and mind doesn't mean its not our problem.
Thursday, November 30, 2006
Windows XP: Stupid Notepad Tricks
Wednesday, November 29, 2006
Software: Download Windows PowerShell 1.0
Windows PowerShell includes more than 130 standard command line tools, with a consistent syntax across all the utilities. To find out how to use PowerShell you can download the Documentation Pack. This documentation includes a 'Getting Started Guide', 'Quick Reference chart' and a 100+ page PowerShell primer.
Note: To install PowerShell, you will need to install the .NET Framework 2.0 on your local computer.
Tuesday, November 28, 2006
Firefox: Clearing Your Browser Information (Privacy)
Firefox and IE have similar caching features, but Firefox has a few extra. Below is a list of Firefox's caching features, and the type of information it tracks:
- File Cache: Stores local copies of web site elements, such as: images, text, etc. This data is used to speed up the browsing experience if you revisit a web page you have already been too.
- Cookies: Small amount of text data that can be placed on your computer by various web sites. This information is used by the web site to hold user information (site preferences, account information, etc.).
- Download History: Tracks the files you downloaded from a web site, and where they're located on your system.
- Web Site History: A list of Web sites that you visited, including the date and time you were there.
- Saved Passwords: When you enter your username and password for a web site, you will be given the option to have the browser manage this information.
- Saved Forms: When you enter information into an online form, this feature tracks your input so that you don't have to enter the same information twice.
- Search Bar History: Tracks all searches you perform with the Firefox search bar.
Monday, November 27, 2006
Internet Explorer: Clearing Your Browser's Cache
Generally, there are only three reasons to clear your browser's cache. One, if you're trying to download a file and you keep getting the corrupted version of that file. Two, to free hard drive space. Three, for privacy reasons, to prevent others from viewing the web sites you visited or files that you downloaded.
In Internet Explorer v6.0 to clear the cache follow the instructions below:
- From the Tools menu, select 'Internet Options...'
- In the General tab, under 'Temporary Internet Files' press the 'Delete Files' button to clear the cache. You can also press the 'Delete Cookies' button to purge your browser's cookies..
- For extra measure
- In the History section you can also press the 'Clear History' button to erase your browser's history of all the web sites that you visited.
- Click on the Content tab, under Personal Information is the AutoComplete button. From here you can delete any saved form data by pressing the 'Clear Forms' button, or erase your saved passwords by pressing the 'Clear Password' button.
- Press the OK button when done.
- From the Tools menu, select 'Delete Browsing History...'
- In the dialog you can individually delete the browser's cache, cookies, history, saved form data or passwords. You can also delete everything by pressing the 'Delete All' button.
Friday, November 24, 2006
Software: Sysinternals Suite Now From TechNet
Microsoft is continuing the Sysinternals legacy of utilities by keeping them available for download on their site. They have also rolled them up into a single suite, this suite contains all the individual tools and help files in one file (8MB in size).
Thursday, November 23, 2006
Free eBook: Defending Yourself in the Information Age
This book explains how to protect your: computer, data, privacy and identity from being stolen. Learn about the latest digital scams, and threats that you will face everyday whether your surfing the Web, or sitting at home reading a book.
Download the book here (1.3M PDF).
Happy Thanksgiving....
Wednesday, November 22, 2006
Internet Explorer: Saving Files from the Web
- Open the Internet Explorer to the web page that has a link to a file that you want to download.
- Right-click the link and select 'Save Target As...' (in Firefox select 'Save Link As...').
- When the 'Save As' dialog displays, choose a name for the file, and the location to save it to.
Tuesday, November 21, 2006
Windows XP: Microsoft Hardware Drivers
Note: The final version of the Windows Vista drivers are supposed to be available in December. If you want to use beta versions of the keyboard and mouse drivers they're available now.
Monday, November 20, 2006
Internet: Zamzar - Free online file conversion
All you do is upload the file, select the format you want to convert it to, enter your email address , and press the convert button. In a few minutes you should receive an email with a link to download the converted document when the process is finished.
Friday, November 17, 2006
Diagnostics: Fixing Problems with your CD/DVD Drive
When troubleshooting any type of computer problem, there are generally two things that you have to do. First, find out if the problem was caused by any recent changes that were made to the system. If so, reverse these changes and see if the problem goes away.
If no modification were recently made to the system, or reversing the change didn't fix the problem. Then the next thing that you need to do is find out if the problem is hardware or software related?
- Hardware related problems:
- Try booting your computer with a bootable CD (such as your OS's installation disk). If you can do this then its a good indication that your drive maybe working properly and the problem might be software related.
- If you're still having problems, open your computer and check your drive's cable and make sure they're properly plugged in correctly on both ends.
- Note: before you open a computer make sure that its unplugged, and that you take appropriate safety precautions before preceding.
- On notebook computer the drive's laser lens could get dirty, from dust or finger prints. On a desktop computer, dust can get into your drive. These contaminants can prevent the laser from being able to read/write to the disk properly. You can try blowing out the drive with compressed air.
- On a notebook computer, place a disk on to the drive's spindle and spin it to see if the disk is spinning correctly. If it doesn't spin easily and/or wobbels, there could be a problem with your drive.
- Software (or system) related problems:
- When burning CD or DVDs its a good idea to make sure that there are no background processes running, they can cause some buffering problems because they're eating up to much CPU time and/or RAM. Check the Task Manager and make sure that you have enough memory and CPU cycles available.
- Did you recently install some new software on your system right before this problem started happening? If so, try un-installing it and try to burn a disk again.
- Did you recently modify the drive's parameters in the Device Manager or your computer's BIOS? If so, revert the settings back to their original state.
- Try un-installing all your CD/DVD burning software that you're using, and use Windows XP built-in CD writer feature. If this works and you're able to burn CDs, then there is a software compatibility problem with your burning software. Check the software manufacturer's web site for updates.
- Try using an alternative CD/DVD burning program like CDBurnerXP Pro. Check if you still have same problems creating a disk using this software. If so, it could be a hardware problem
- If the disks you're creating are only readable on your computer and not any other system, the problem could be with your CD/DVD burning software. If you're software doesn't close the session on the disk, it may not be readable on another computer. Check how your CD burning software is configured to create disks.
- Other suggestions
- Search the web for your drive's model number and the keyword "Firmware", sometime manufactures will release updates to their drive's firmware.
- Try another brand of media, you might have gotten a hold of a bad batch of disks. If you use really cheap disk, this situation is not too uncommon.
Thursday, November 16, 2006
Software: Process Monitor v1.01
Process Monitor is a great utility for performing advanced system monitoring and getting real-time file system, Registry and process/thread activity. The utility now incorporates the features of two other Sysinternals utilities, called Filemon and Regmon.
Process Monitor runs on Windows 2000 (SP4), XP (SP2), 2003 (SP1), and Vista. Its also supports both x86 and x64 versions of Windows. Check out the web site for more information
Wednesday, November 15, 2006
Software: Sysinternals New Home...
Microsoft recent acquired Sysinternals, and hired its creators Mark Russinovich and Bryce Cogswell in July, 2006. Now they have publish the Sysinternals tools on their web site. In fact the old Sysinternals web site now redirects people to the Microsoft version of the site.
Since joining Microsoft, a new generation Process Explorer has been released called 'Process Monitor' which in fact combines a few utilities into one package.
Tuesday, November 14, 2006
Security: Microsoft Patch Tuesday (November)
Microsoft generally rates the severity (such as: critical, important, etc.) of each of the patches. This month there are five patches that are marked critical, and one patch that is marked important.
For the average user, if you have Automatic Updates enabled your computer will download these updates for you in the background. Then when you shutdown these patches will be installed, or if you leave your computer on overnight they will automatically be installed and your system rebooted.
Warning: Any unsaved work will be lost if your system is rebooted...
To keep your computer updated, if you don't have 'Automatic Updates' turned on I would recommend that you enable it as soon as possible. Also if you have enabled this feature, and you leave your computer on overnight I would save all your work before you leave for the day.
To enable Automatic Updates:
- From the Start menu, select the Control Panel folder.
- Double-click the System applet in the control panel folder.
- Click the 'Automatic Updates' tab.
- Check the 'Automatic (recommended)' option. (optional: if you don't like this feature, you can set it to: 'download but not install the update', 'just notify you', or 'disable this feature altogether' [not recommended])
- Press the OK button when done.
Note: For the latest Microsoft Security Bulletins, check out this site.
Monday, November 13, 2006
Article: Alarm Raised for Critical Broadcom Wi-Fi Driver Flaw
This seemed like the hot topic of the day. Basically there's a stack-based buffer overflow exploit in the Broadcom BCMWL5.SYS wireless device driver. Basically if you use your Wi-Fi card to hookup to the Internet in a public place, you could theoretically have your computer taken over by this exploit.
Broadcom has released a fixed driver to its partners, but the availability of fixes appears to be limited. Check with your Wi-Fi card manufacture to find out if you're affected.
Friday, November 10, 2006
Article: Microsoft: Vista RTM a 'Significant Milestone'
Windows Vista and Office 2007 will be coming soon to a store near you. Windows Vista is the most significant upgrade to this OS since Windows 95. The desktop, and Windows Explorer have several new features that may take some time to get use to.
Overall, I really like Vista it has been a very stable OS. When it first ships the greatest problem I would expect that most people will have is driver availability for certain devices.
There is a lot of driver support build into Vista already. Although, for some devices you might have to wait for manufacture to release updated drivers.
Thursday, November 09, 2006
Windows XP: Turning off the 'New Programs Installed' Notice
To disable this feature, follow these instructions:
- Right-click the Start button, and select Properties.
- On the Start Menu tab, press the Customize button.
- Click the Advanced tab.
- Under 'Start Menu Settings,' uncheck the 'Highlight newly installed programs' checkbox.
- Press the OK button.
Wednesday, November 08, 2006
Internet: Live Search 3D Maps
3D views are available for the following cities:
- Atlanta
- Baltimore
- Boston
- Dallas
- Denver
- Detroit
- Fort Worth
- Houston
- Las Vegas
- Los Angeles
- Philadelphia
- Phoenix
- San Francisco
- San Jose
- Seattle
Tuesday, November 07, 2006
Software: Firefox 1.5.0.8 is Now Available
- Running Script can be recompiled
- RSA signature forgery (variant)
- Crashes with evidence of memory corruption
Monday, November 06, 2006
Security: ShieldsUp and LeakTest
Most commercial firewalls that you can buy today are two-way firewalls which means that they block threats from the Internet, but they also alert you to programs that is trying to communicate with the Internet. Most of the time you're only going to see legitimate requests from applications (such as your browser, IM client, etc.) requesting access to the Internet.
Although there are times that you might find that there is a rouge application that is installed on your computer making a request. This is when you should suspect if your computer is infected by some type of malware.
Gibson Research offers to great utilities that can help you evaluate how well your computer's defenses are protecting you. The first utility is called ShieldsUp which checks your firewall for open, closed and stealth ports.
Quick lesson about TCP/IP: When communicating with the TCP/IP protocol (everything on the Internet uses this protocol to talk to each other) with another device there are two things that you have to know. The remote device's IP address and the TCP port that you want to communicate with. A TCP port is like a port hole on the side a ship, when its open it can allow something in (i.e.: air, water, birds, etc.), when its closed then nothing can get in.Ideally you want all the ports on your computer to be stealth which means when hackers and malware are scanning for vulnerable computers they won't be able to find you. While closed ports are not as good as stealth ports because they tell the hacker or malware that there is a computer at a specific IP address. Although, since the port is closed, there is nothing that they can do with it.
The second utility is called LeakTest, which is a very simple program that makes a request to the GRC's web server. If your firewall let's the program make the request without alerting you then your firewall doesn't block unknown outbound connections. These connections can be used by malware to 'leak' data about you out of your computer without you knowing about it.
Friday, November 03, 2006
Software: EverNote (Note Organizer)
There are several different programs available on the market to do this, but there are two I would suggest that you check out. The first one is called OneNote from Microsoft, its part of their Office suite. The second program is called EverNote. Both of these programs can capture, search, and allow you to organize several different types of data (i.e.: text, web pages, e-mail, images, video, and more.)
EverNote comes in two versions, free and paid. Both versions are featured pack, but he paid version has three main features that the free version doesn't:
- Synchronizing your notes with a USB flash drives or other types of removable media.
- Handwriting, and shape recognition.
- The ability to search in handwritten notes.
Thursday, November 02, 2006
Video: First look at Microsoft Office Live
The video production quality is sub-par, but it gives you a quick introduction to the Microsoft Office Live service.
Wednesday, November 01, 2006
Software: Microsoft is Giving Away a Free Accounting Application
Some of the new functionality includes: creating invoices, quotes, receipts, and expense tracking. Some of the other features of the program include:
- Enter data once and share it seamlessly with other Microsoft Office system programs
- Manage payroll and taxes with ADP's integrated payroll service
- Store and organize all your customer, vendor, employee, and financial information in one place
- Get business insights with over 20 customizable reports
- List items on eBay, track sales activity, and download and process orders
- Monitor your customers' business credit in real-time through Equifax
- And more.
Tuesday, October 31, 2006
Windows Media Player 11 Hits the Street
Windows Media Player 11 is finally here. It has a slick new interface and lots of new features. Read the article to get a quick run down of some of the new functionality.
The player is available for download here.
Monday, October 30, 2006
Free and Low Cost Office Suites (and other stuff)
There are several options available to you. Some of these suites require that they be install on your local computer, and others can be run from within your browser.
Personally I am a big fan of Microsoft Office, and I have a hard time using anything less. The one problem with Office is that its not free or low cost.
If you just have basic word processing needs, such as writing letters to your friends and family, or creating simple spreadsheets or presentations. Then Microsoft Office might be over kill for you, there several other choices available that might be a better fit for your needs.
Out of all the free, low cost, or online office suites available, OpenOffice.org is the best IMHO. Then after that I would start to look at everything else and see what fits your needs. Whatever you look at, make sure its has the features that you're going to use.
All these tools are pretty good for doing basic things like creating a document, managing numbers, etc. Although, for tasks that are more complicated, you're going to need a real office suite like OpenOffice.org or Microsoft Office.
Office Suites
Browser Based:
- ThinkFree: A Java-based browser office suite. Includes word processor, presentation and spreadsheet application.
- Google Docs & Spreadsheets: An AJAX-based browser office suite. Includes a word processor and spreadsheet application.
- ZOHO: An AJAX-based browser office suite. Includes a word processor, presentation spreadsheet application, and more.
- OpenOffice.org: One of the best office suites available. Includes a word processor, presentation and spreadsheet application.
- AbiWord: A free word processor application.
- Dia: An open source vector graphic program.
- GIMP: An open source bit-map drawing program.
- Scribus: An open source page layout program.
- Meebo: A browser based universal instant messaging client. Supports: AIM, ICQ, MSN Messenger, Yahoo Messenger, Jabber and GTalk.
- Trillian: If you have multiple accounts across several IM services this is a great IM client. Supports: AIM, ICQ, MSN Messenger, Yahoo Messenger, and IRC.
Browser Based:
- Gmail/Google Calendar: Provides: e-mail, calendaring, contacts and notes.
- Yahoo! Mail: Provides: e-mail, calendaring, contacts and notes.
- Contact Office: Provides: email, calendaring, address book, fax, SMS, phone calls, etc.
- Thunderbird: An e-mail client, with spam filtering.
- Sunbird: Calendaring with a task manager.
Below are some extra resources that you may need in your day-to-day activities.
Software:
- GnuCash: Personal and small-business financial-accounting software.
- Free Templates: Free label templates for: Avery, CDs, address, mailing, shipping, etc.
- 1001 Free Fonts: Thousands of free fonts are available for download.
- Answer.com: Need information about a word or subject, this site includes dictionary, thesaurus, encyclopedia (uses Wikipedia), and more.
- Currency Converter: Lookup current exchange rates for just about any currency.
- Martindale's Reference Desk: A great collection of links to different types of references available on the web.
- Martindale's On-Line Calculators: A great collection of links to different types of calculators available on the web.
- RefDesk: A great collection of reference resources that are available on the Web.
- Unit Converter: Convert just about any numerical data from one unit type to another.
- World Clock: A web-based world time clock.
- Yearly Calendar: A web-based yearly calendar.
Saturday, October 28, 2006
Network: Error Message - "Network Cable Unplugged"
Until the day they get a message that says 'Network Cable Unplugged.' It sounds simple and could be but this same message could also mean something more then the cable is unplugged. This same message could mean that you have a short in your cable, your network card has stopped functioning, etc.
Follow the steps below to help diagnose this problem:
- Verify the cable is plugged in at both ends, press it in see if you hear a click. Check your computer and see if the message goes away. If it doesn't unplug the cable at both ends, then plug it back in.
- If this is a new cable, make sure that its not a crossover cable (check the bag that it came in) you need a straight through network cable. Also some network switches have an uplink port or a button to make a port an uplink port. If the uplink button is enabled disable it, this is only needed if you're hooking two switches together without a crossover cable.
- When the cable is plugged in you should see a green light (or even a flashing green or amber light) on the switch and on your computer. If you're not getting these lights after you check the cable in the previous step, try changing out the cable.
- If you're not getting any lights on your network switch, make sure its plugged in and getting power. Most switches have some type of diagnostic lights, if you don't see them the wall plug, power transformer, or network switch could be bad.
- If you know your switch is working, try plugging the cable into a different port on it. Its not to uncommon for a port to go bad on the network switch or an Ethernet card. If you have another computer that you can plug the cable into try that. If you know the port is working on the network switch, try using a different Ethernet card in your computer.
- Before you switch out the Ethernet card in your computer, check to see if you can find it in your Windows Device Manager. If you do see it you can try to uninstall and reinstall it again (this will require that you already have the driver for this device on your computer). If you don't see your network card in the Device Manager try downloading the driver from the manufacture's web site.
Wednesday, October 25, 2006
Software: Microsoft Windows Defender Released
So far, I have not been infected by any virus or spyware, but I can't give all the credit to the scanner. I avoid downloading stuff from the Web that I shouldn't, that is the best way to prevent getting any type of malware.
Below is a list of some of the new features of the scanner:
- Enhanced performance in the new scanning engine.
- A simplified user interface and alerts.
- Globalization and localization features, with multiple language support.
- Support for Microsoft Windows XP Professional x64 Edition.
- Automatic cleaning according to your settings during regularly scheduled scans.
Tuesday, October 24, 2006
Article: Firefox 2.0 Scheduled For Release on Tuesday
I have been playing with the release candidate of this browser for a few weeks now. It has some nice new features, but their not revolutionary.
I have one major complaint about this version of Firefox, several of my favorite extensions stopped working. So be prepared to be disappointed here.
Personally, I believe that the ideas for most of the new features in the browser were borrowed from the more popular extensions. Below is a list of some of the new features:
- Phishing filter warns you when you're visiting a fake web site.
- A new search feature that displays suggestions as you type your search request.
- A session manager that restores the windows and tabs you had opened before a crash.
- A spelling checker that spell checks your input into web forms.
- Better RSS support.
Monday, October 23, 2006
Wireless: Optimizing and Troubleshooting a Wireless Network Connection
it adds an entry for that network in to the 'Preferred Network' list. This list is meant to remember your network settings when you move from wireless network to network. The problem is that if you move between a lot of different wireless networks this list can get really filled up with a lot of junk that can slowdown your network connection time.
Another problem that happens often is that you can find yourself constantly being connected to a wireless network that you don't want to be connected to. This problem is caused by the fact that the entry for the wireless network that you don't want to be connected has a higher order of preference then your preferred network.
To fix both of these problems:
- From the Control Panel folder, open the Network Connection folder.
- Right click on the Wireless Network Connection icon, and select Properties
- Click the Wireless Networks tab.
- In the 'Preferred Networks' list, highlight and delete any wireless networks that you don't use. If there is a network that you use more often then others. Highlight the network and press the 'Move Up' button to move it to the top of the list.
- Press the OK button when don't
Thursday, October 19, 2006
Windows XP: Internet Explorer 7 is now available...
Some of the new improvements in the browser include: security protection, a redesigned user interface, and a development platform. Below is a high level list of the major new features:
- Phishing Filter (reports if a web site is not who it really is)
- RSS Reader (allows you to read RSS feeds in the browser)
- Tabbed browsing (open multiple web pages in a single window)
- Toolbar search box (quickly search from the toolbar)
- Advanced printing (optimized web page printing)
- Security Status Bar (displays different colors in the status bar to notify you how safe the web site might be)
- Privacy Cleaner (quickly deletes your browser cache, cookies, and other data that might contain personal information)
- And more...
Wednesday, October 18, 2006
Security: Rootkits Tools
There are several types of malware (viruses, Trojan horses, rootkits, etc.) that are in the wild on the Internet. Some types of malware will find and infect you if you're not running a firewall, others will disguise themselves in the form of an attachment. You can even get infected by visiting the wrong web site if your browser is vulnerable.
Rootkits are the type of malware that doesn't take no for an answer, they will try to exploit every trick they can to get administrator access to your computer. Then once they become an administrator they will deploy their payload.
Most anti-virus and anti-spyware scanners don't properly find rootkits, because they're generally very difficult to detect. Below are some anti-rootkit tools (some free, and others are fee based) that you can run to see if your system is infected by this type of malware.
- Sysinternals: RootkitRevealer (free) - I have talked about this scanner before in a previous article. Although its still a good tool for detecting this type of malware, but it can't remove it.
- F-Secure: BlackLight (free trial until 1/2007) - This application seeks out and tries to remove any rootkits it finds installed on your computer.
- Sophos: Anti-Rootkit (free) - I have talked about this scanner before in a previous article. This application seeks out and tries to remove any rootkits it finds installed on your computer.
Windows XP: Automate the Disk Cleanup Tool
Now, I am going to show you how to automate this process. Its relatively easy to do, all you have to do is follow the instructions below:
Configuring the Disk Cleanup tool:
- From the Run... command, type "cleanmgr /sageset:1" and press the OK button.
- You can have up to 0 - 65535 profiles, all you have to do is change the number after '/sageset'. Make sure you remember the number you selected for the profile you will need it for the next section.
- When the Disk Cleanup dialog displays, select or unselect the type of files that you want to remove when the tool is run.
- Press the OK button.
- From the Run... command, type "cleanmgr /sagerun:1" and press the OK button.
- Make sure to use the session number (i.e.: 1 in the example above) for the Disk Cleanup profile you created in the previous section.
The 'cleanmgr /sagerun:1' command can be run from the MS-DOS prompt, added to a script, or run from the 'Scheduled Tasks' feature on a regular basis.
Tuesday, October 17, 2006
Software: Changing the World with Your Screen Saver
The screen saver utilizes the unused processing power of your computer, as a part of a large distributed computing cluster. These clusters can be composed of thousands (or more) of computers working together for a common goal. The way these large clusters work is each computer downloads a small part of a larger problem, and computes the data and sends the results back to the master computer.
Below is a list of some of the projects that are available:
- boinc.berkeley.edu: Stands for 'Berkeley Open Infrastructure for Network Computing', here is a brief list of some of the current projects: Climateprediction.net, Seasonal Attribution Project, BBC Climate Change Experiment.
- folding.stanford.edu: Searches for treatments for Alzheimer's, Huntington's, and other related diseases.
- grid.org: Searches for treatments for cancers, and other diseases.
- SETI@home: Analyze radio telescope data in the search for extraterrestrial life.
- www.worldcommunitygrid.org: Searches for treatments for cancers, and other diseases.
Thursday, October 12, 2006
Windows XP: Disabling Services and Devices Based on Hardware Profile
To disable services based on a hardware profiles:
- From the 'Administrative Tools' folder, double-click on Services.
- Double-click the service you want to modify
- Click the Log On tab in the properties dialog
- Click disable for the selected Hardware Profile.
- Open the 'Device Manager'
- Double-click the device you want to modify.
- In the General tab under the 'Device Usage' label select 'Do not use this device (disable)' option
- Press the OK button.
Wednesday, October 11, 2006
Windows XP: Recovering from a Failed Driver Installation
- Uninstall the device driver, restart the computer and try reinstalling it again.
- Try using the Driver Roll Back feature.
- Try using the System Restore feature.
- From the Start menu > All Programs > Accessories > System Tools > System Restore. Follow the instructions in the wizard.
- Reboot the computer, press F8 at startup, and select 'Last Known Good Configuration' and press the Enter key.
- From the MS-DOS prompt, type "sfc.exe /scannow" (this runs the System File Checker). It verify the protected system files, and if problems are found it will revert them to a previous version.
Tuesday, October 10, 2006
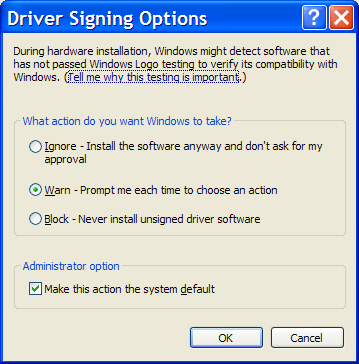
Windows XP: Driver Signing
Drivers can come from many different sources, like an installation CD, a web site, or other various sources. Some device drivers are not digitally signed by Microsoft, which could mean that they may not have been tested as thoroughly as they could have been. There's a greater chance that they could effect the stability of your system because of unknown compatibility issues.
To configure how these signed and unsigned drivers are handled by the OS, you need to open the 'Driver Signing Options' dialog:
- Open the Control Panel folder.
- Double click the System applet.
- Click the Hardware tab.
- Press the 'Driver Signing' button.
- Ignore (Allows the installation of any files, signed or not.)
- Warn (Displays a warning message that the driver being installed is not signed.) [Default]
- Block (Prevents the installation of unsigned drivers).
Monday, October 09, 2006
Windows XP: Ways to Install New Device Drivers
- Setup Program: This is software that comes with your new device. To install this software, generally requires putting a CD/DVD in your computer or downloading the setup application from the device manufacturer's web site.
- Note: Some devices require that the installation software is installed first before you hook the hardware up to your computer. This is done to make sure the device is properly detected.
- Booting Your Computer: Every time Windows starts it scans the system for new hardware that might have been added or removed since it was last on. After the system is fully booted, if new hardware is detected it will check if the system already has the appropriate driver for it. If not, it will request that you provide the location of the driver it needs.
- New Hardware Scans: Sometimes after you boot Windows, you may not have the right drivers for new hardware that was added at that moment. After you get the right driver, you use the Add Hardware Wizard (select the Add Hardware icon in the control panel) to manually perform the hardware-detection and installation process to install the appropriate device driver.
- Manual Installation: Sometimes device drivers don't come with an installation program, but instead they come with .INF files. You can right-click these files and choose Install to add these new drivers.
Friday, October 06, 2006
Security: Simplifying Web Site Logins
I recently came across a very cool browser-based utility that simplifies using, creating and remembering strong passwords across any web site. All you have to do is create a master password that only you know, and give the site a URL (such as: http://www.google.com), it will then create a unique password for that web site. You can also create a bookmarklet (JavaScript embedded in to a bookmark) that you can store in your browser links bar, that can automatically generate a password for a site that your visiting based on your master password.
The way this utility works is by using JavaScript on a local web page loaded in your browser (no information is sent to the remote server). The script then uses MD5 to create a one-way hash based on your master password and the domain of the web site that you're going to use it for. Only the first eight (or more) characters of the hash are selected, so its impossible to break the hash because not all the information is used.
Thursday, October 05, 2006
Windows XP: Turning Off the Language Bar
- Open the Control Panel folder.
- Double-click 'Regional and Language Options' applet.
- Click the Languages tab.
- Under 'Text services and input languages', press the Details button.
- Under Preferences, press the 'Language Bar' button.
- Uncheck the 'Show the Language bar on the desktop' checkbox.
- Press the OK button twice.
Wednesday, October 04, 2006
Security: Internet Privacy is an Oxymoron
Did you know that there is no such thing as true anonymity or privacy on the Internet? All you can do is mask your identity, and make it difficult for someone to know who you are. Although, in most cases its still possible for someone to track and identify you with enough work.
There is a lot of information about you that is leaked by your own personal Internet activities (such as surfing a web site, posting on forums, etc.). Then your computer and its applications (such as your browser, IM client, etc.) are doing their own fair share to help leak more information.
Anything that contains your name, address, etc. Is known as 'personally-identifiable information' (PII), because it can personally identify you directly. This information is generally provided by you to some web site or service (such as Amazon, eBay, etc.) that you may use regularly.
Any of the information (PII or not) is used to profile how you surf the web, what you buy, and other types of demographic analysis. All most all of this tracking is perfectly legal, and you even grant companies permission to do this when you agree to use a web site through its 'terms of service' or 'privacy policy' that you don't read.
Information Leaked by your Applications
As I said earlier, when you visit a web site there is certain types of information about you that is revealed by your computers applications. A lot of this information (such as your browser cookies) are needed by web-based applications to be able to customize your experience.
Below is a brief list of some of the information a web site can know about you, just by visiting it with a regular browser and Internet connection:
- The type of browser you're using, a long with information about its features. For example: what version of: Java, JavaScript, Flash and other applications you have installed (see: BroswerSpy).
- This doesn't include the information in the HTTP header, which includes information about your browser and the web page you requested from a web site (see the following article for more information).
- There is information in the HTTP header called the 'referer', that also gives the web site your visiting, the last URL of the web site you're coming from. Here is an example, of some of the information a site can see about you.
- Browser cookies and web beacons (an invisible 1x1 graphic on a web page with a unique id embedded in to its name), which can be used identify your computer across different web sites. This technology is generally used by advertising and marketing companies to track and profile your browsing activity to better serve you ads.
- As more web sites become interactive, browser cookies are used to track your web site session information. If you turn off the cookie feature, you can prevent certain web sites from working properly for you.
- Web beacons have been used by spammers to track if you open up an email message, and to see if a email address is valid. Although, most modern email clients prevent images from being downloaded automatically which help prevent information about you from being leaked.
- Your browser keeps local copies of all the web pages you visited in its cache, along with a history of all the URLs you visited. Some browser's like Firefox keep track of the files you downloaded, and the keywords you typed into the search toolbar. Then there is the saved forms information (known as AutoComplete in IE), and saved password feature. This information is used to improve the broswer's user experience, but also can become a privacy issue in some cases.
For example, your instant message client may keep logs of all your conversations. Your e-mail client, keeps all the messages that you received and sent. Your VoIP client keeps a log of all the calls that you make.
Even if you clean all this information off your local computer, your application's service provider has logs and/or copies of it in their servers and databases. Its not uncommon for them to use this information to profile usage habits of their users. All this information is also available to local and federal law enforcement generally with the use of a search warrant.
Generally, no matter what network enabled application your using, the following information is always going to be left about you on some server somewhere.
- Once someone knows your computer's IP address, its possible to isolate the ISP, and therefore the city, state/province, and country your computer's from (see: IP Address Locator).
- Local and federal law enforcement with the use of a search warrant can force the ISP to release your identity, based on your computer's IP address.
- When you visit a web site, information is stored in the web server logs of the time you visited the site, your IP address, which pages you viewed, and sometimes what you searched for on that site (see: Omniture).
- Think about this, all your favorite search engines keep all the information that you searched. If you have a personal account on a site like Google, Yahoo, etc., they can directly tie this information back to you.
- For example: "On August 4, 2006, AOL released three months of search history for 650,000 users to the public. Although the searchers were only identified by a numeric ID, the New York Times discovered the identity of several searchers." (excerpt from the Wikipedia)
- Anytime you visit a web site using it's domain name your computer needs to lookup the IP address of the remote server through some DNS server request. This information is then logged on that computer.
- When you're at work, and you search the Internet your companies web proxies and firewall can track all types of Internet activity. Plus in the U.S.A. any information on your computer, or in your e-mail is property of the company.
With all the data stored on computers these days, a new area of computer criminal science has been created called 'digital forensics'. These are law enforcement personnel specially trained to find and retrieve specific information off a computer.
The tools that these people use are good at extracting the data they want. Generally the programs we use everyday are really good at leaving digital bread crumbs all over your computer's hard drive about everything that you do. These digital forensics tools are designed to leverage this information
On a side note, about digital forensics tools. Did you know that by using a pattern analysis program you can predict if something was written by a man or a women with almost 70% accuracy.
The way this technology works is by analyzing the words used in a message and assigns different values to them to determine if the text was written by a man or women. More information can also be determined by your writing style beside gender, such as your nationality based on the words that you use.
To see this tool in action, check out Gender Guesser or Gender Genie. With technology like this, it means that any of those anonymous posting or e-mail you might have created are becoming a lot less anonymous.
Note: This technology was created by Dr. Neal Krawetz of Hacker Factor Solutions.
Tuesday, October 03, 2006
Article: Firefox Zero-Day Code Execution Hoax?
Monday, October 02, 2006
Windows XP: Accessing the Windows Update Catalog
There can be several reasons why you would want to do this, for example: you have a slow modem at home and you want to get your updates from a faster computer. Or, if you're a systems administrator at a company, and you need to update Windows clients or servers.
Whatever the reason, here is how you can do it.
- Open Internet Explorer (this won't work from Firefox), and go to "http://v4.windowsupdate.microsoft.com/catalog"
- Click the link "Find updates for Microsoft Windows operating systems" or "Find driver updates for hardware devices"
- If you selected the find updates for operating system, you will need to select the OS which you're looking for the updates. Press the Search button to continue.
- Select the category, and then select updates that you want to get.
- Click the "Go to Download Basket" link.
- Press the Browse... button to select the download location on your local computer.
- Press the 'Download Now' button.
- Choose if you want to accept the licensing agreement, then press the appropriate button.
Friday, September 29, 2006
Firefox: Open Multiple Home Pages
For example:
http://www.google.com | http://yahoo.com
To set the home page in Firefox (I am assuming you already have it open):
- From the Tools menu, select Options...
- In the Location(s) field, enter the URLs you want to use and separate them with a "|" (no quotes).
- Press the OK button when done
Thursday, September 28, 2006
Security: Patch Your System Now
If you have not patched your system, do it now at Microsoft Update. If you have the Windows Automatic Update feature enabled to download and install the patch, you should have it by now. If you don't have this Automatic Update feature enabled on your computer and want it, the instructions for setting it up are available in this article.
For more information on the patch see the following page.
Wednesday, September 27, 2006
Windows XP: Microsoft Guided Help
Note: Currently there only about 20+ MSKB articles that support this feature, although I hope more will be added soon. Look for the following icon:If you're an advanced user, this feature will not be too helpful. These tutorials are targeted at the novice user who wants some one to show them what to do, and how to do it. Although if you know someone who can benefit from this feature, I would email them the link to the article.in the search results to find articles that contain this feature.
When you find an MSKB article that contains the Guided Help feature. All you have to do is download the program from the article and then execute it. After accepting the licensing agreement, the program will give you screen clues on what to do and what to click.
For more information about Guided Help check out this MSKB page.
Tuesday, September 26, 2006
Software: Sophos Anti-Rootkit
Sophos is offering a free Anti-Rootkit scanner, that will seek out and try to remove this software if its installed on your computer. The Sophos Anti-Rootkit scanner can be run from the GUI (Graphical User Interface), or the command line.
Monday, September 25, 2006
Reference: Types of Memory card
For example the SD form factor is the most popular, while the CF-II allows you to use Microdrives. Some media card types such as SmartMedia never took off.
Personally, one of my selection factors for buying new electronics is that the device needs to support SD cards. I hate having devices that can't support the same type of removable media. This is handy when you need to be able to off load the media to another device quickly.
Below is an excerpt from an Wikipedia article on the different type of media cards available. You might notice some media card form factors that you may never have heard of before, I know I did. If you want more information on any of them just click the link.
| Name | Acronym | DRM |
|---|---|---|
| CompactFlash I | CF-I | None |
| CompactFlash II | CF-II | None |
| SmartMedia | SM / SMC | None |
| Memory Stick | MS | MagicGate |
| Memory Stick Duo | MSD | MagicGate |
| Memory Stick Micro M2 | M2 | MagicGate |
| Multimedia Card | MMC | None |
| Reduced Size Multimedia Card | RS-MMC | None |
| MMCmicro Card | MMCmicro | None |
| Secure Digital Card | SD | CPRM |
| miniSD Card | miniSD | CPRM |
| microSD Card | microSD | CPRM |
| xD-Picture Card | xD | None |
| Intelligent Stick | iStick | None |